The Azure Console Button Is a Lie (And You Don't Need AMA)
2025-10-09 · ~29 min read
VMware admins: That 'Connect' button isn't console access. Serial Console is hidden in Help > Boot Diagnostics, works without networking, and doesn't require Azure Monitor Agent. Here's what Microsoft didn't tell you.
I clicked the Connect button in Azure Portal. The VM won't boot. The Console requires networking to work. The VM's network is broken. This is useless.
If you've migrated from VMware to Azure, you've had this moment. You need console access—the real console, the one that works when networking is dead, the one you used in vSphere to see boot messages and fix broken VMs. You click "Connect" in Azure Portal expecting VMware console behavior.
It doesn't work.
Then someone tells you: "Install Azure Monitor Agent for console access."
Also wrong.
The Problem: VMware Admins Are Confused
In VMware vSphere:
- Right-click VM → Open Console
- See actual screen output (BIOS, boot loader, POST messages)
- Works even when networking is completely broken
- True out-of-band access to the hypervisor
- Fix boot issues, network misconfigurations, locked accounts
In Azure Portal (the button everyone clicks):
- Click VM → Connect
- Launches Azure Bastion or RDP/SSH connection
- Requires networking to work ❌
- Completely useless if VM won't boot or network is misconfigured
- Not true "console" access
Result: "Azure sucks, VMware was better!"
Not true. Azure has the equivalent feature. It's just hidden in a weird place and poorly documented.
Why Azure Did This (Context Matters)
Azure actually has TWO different "console" features with confusing names and placement:
- Connect button (VM Overview page)
- Launches Bastion/RDP/SSH
- Requires working network
- Used for normal remote access
-
99% of daily VM access
-
Serial Console (buried in Help → Boot Diagnostics)
- True console access via COM1 serial port
- Works when networking is broken
- Hypervisor-level access
- The VMware console equivalent you actually need
Most VMware admins never find Serial Console. They click Connect, it fails, and they assume Azure doesn't have console access.
The AMA Confusion: "Do I Need Azure Monitor Agent?"
Short answer: NO (for console access)
This is the most common misconception when migrating from VMware. Here's why the confusion exists:
What Azure Monitor Agent (AMA) is actually for:
- Collecting metrics → Azure Monitor
- Sending logs → Log Analytics
- VM Insights, Update Manager, Change Tracking
- Guest-level monitoring and management
What Serial Console uses:
- Boot Diagnostics (hypervisor screenshot capability)
- Serial port access (COM1, built into Azure fabric)
- Storage account (for boot screenshots only)
- Zero agents required
Why the confusion:
- Azure documentation pushes AMA everywhere
- "Best practice" guides say "install AMA on all VMs"
- Admins assume AMA is required for basic functionality
- Reality: Serial Console existed BEFORE AMA was created
The timeline:
- Serial Console: Launched 2018 as hypervisor-level feature
- Azure Monitor Agent: Released 2021 as monitoring solution
- They are completely separate technologies
Requirements: What You Actually Need
Here's what Serial Console requires, with the AMA confusion cleared up:
| Requirement | Required? | Purpose | How to Enable |
|---|---|---|---|
| Boot Diagnostics | ✅ YES | Enables serial port access + screenshots | Set-AzVMBootDiagnostic -Enable |
| Serial Console Feature | ✅ YES | Subscription-level feature flag | Register-AzProviderFeature -FeatureName "EnableSerialConsole" |
| Storage Account | ✅ YES | Stores boot diagnostic screenshots | Create storage account, reference in boot diagnostics |
| VM Must Be Running | ✅ YES | Can't access console on deallocated VM | Start the VM |
| Azure Monitor Agent | ❌ NO | Monitoring/logging only - not console access | N/A - Don't install for Serial Console |
| Network Connectivity | ❌ NO | Serial Console works when network is broken | N/A - This is the whole point! |
| RDP/SSH Working | ❌ NO | Serial Console is the backup when these fail | N/A |
OS-Specific Requirements
Windows VMs:
| Requirement | Required? | Default State | Notes |
|---|---|---|---|
| SAC Enabled | ✅ YES | ✅ Enabled on Azure images | Emergency Management Services (EMS) |
| Admin Password Known | ✅ YES | 🔒 You set this | Can reset via SAC if locked out |
| EMS Service Running | ✅ YES | ✅ Running by default | Get-Service EMS to verify |
Linux VMs:
| Requirement | Required? | Default State | Notes |
|---|---|---|---|
| Serial Console in GRUB | ✅ YES | ✅ Enabled on Azure images | Console output on ttyS0 |
| Root/Sudo Access | ✅ YES | 🔒 You configure this | Need privileges to run commands |
| Console Configured | ✅ YES | ✅ Default in Azure images | Check /etc/default/grub |
What You DON'T Need (Common Misconceptions)
| Feature | Do You Need It? | Why People Think They Need It |
|---|---|---|
| Azure Monitor Agent (AMA) | ❌ NO | Azure pushes it for everything; docs unclear |
| Log Analytics Workspace | ❌ NO | Confused with monitoring requirements |
| Azure Bastion | ❌ NO | Different service; requires working network |
| VM Extensions | ❌ NO | Serial Console is hypervisor-level |
| NSG Allow Rules | ❌ NO | Serial Console bypasses network entirely |
| Public IP Address | ❌ NO | Access through Azure Portal, not network |
Where Serial Console Actually Lives
Location in Azure Portal:
VM → Help → Boot diagnostics → Serial console
NOT in any of these places (where you'd expect it):
- ❌ VM Overview → Connect (that's Bastion/RDP)
- ❌ VM → Operations (no console there)
- ❌ VM → Monitoring (that's metrics)
- ❌ VM → Extensions (no console extension)
Why it's hidden there:
Microsoft categorizes Serial Console as a "troubleshooting tool" not a "daily operations tool." In VMware, console access is front and center because it's used regularly. In Azure, Microsoft expects you to use Bastion/RDP for 99% of access, and Serial Console only for emergencies.
Enable Serial Console: Complete Setup
Step 1: Enable at Subscription Level (One Time)
# Enable Serial Console feature for entire subscription
Register-AzProviderFeature -FeatureName "EnableSerialConsole" `
-ProviderNamespace "Microsoft.SerialConsole"
# Verify feature registration status
Get-AzProviderFeature -FeatureName "EnableSerialConsole" `
-ProviderNamespace "Microsoft.SerialConsole"
# Expected output:
# FeatureName ProviderName RegistrationState
# ----------- ------------ -----------------
# EnableSerialConsole Microsoft.SerialConsole Registered
Note: Feature registration can take 5-15 minutes. You only do this once per subscription.
Step 2: Create Storage Account for Boot Diagnostics (If Needed)
# Create storage account for boot diagnostics
New-AzStorageAccount -ResourceGroupName "rg-shared-001" `
-Name "saproddiag001" `
-Location "eastus" `
-SkuName "Standard_LRS" `
-Kind "StorageV2"
# Note: Storage account names must be globally unique and lowercase
Storage account naming rules:
- 3-24 characters
- Lowercase letters and numbers only
- Globally unique across all of Azure
Step 3: Enable Boot Diagnostics on VMs
# Enable boot diagnostics on single VM
$vm = Get-AzVM -ResourceGroupName "rg-prod-001" -Name "vm-app-001"
Set-AzVMBootDiagnostic -VM $vm -Enable `
-ResourceGroupName "rg-shared-001" `
-StorageAccountName "saproddiag001"
Update-AzVM -VM $vm -ResourceGroupName "rg-prod-001"
Step 4: Enable at Scale (All VMs in Subscription)
# Enable boot diagnostics for all VMs in subscription
$storageAccount = "saproddiag001"
$storageRG = "rg-shared-001"
$vms = Get-AzVM
foreach ($vm in $vms) {
Write-Host "Enabling boot diagnostics on $($vm.Name)..."
$vmFull = Get-AzVM -ResourceGroupName $vm.ResourceGroupName -Name $vm.Name
Set-AzVMBootDiagnostic -VM $vmFull -Enable `
-ResourceGroupName $storageRG `
-StorageAccountName $storageAccount
Update-AzVM -VM $vmFull -ResourceGroupName $vm.ResourceGroupName
Write-Host "✓ Completed: $($vm.Name)" -ForegroundColor Green
}
Verification: Check Serial Console Status
# Check Serial Console feature status
$feature = Get-AzProviderFeature -FeatureName "EnableSerialConsole" `
-ProviderNamespace "Microsoft.SerialConsole"
if ($feature.RegistrationState -eq "Registered") {
Write-Host "✓ Serial Console enabled at subscription level" -ForegroundColor Green
} else {
Write-Host "✗ Serial Console not enabled. State: $($feature.RegistrationState)" -ForegroundColor Red
}
# Check boot diagnostics on specific VM
$vm = Get-AzVM -ResourceGroupName "rg-prod-001" -Name "vm-app-001"
$bootDiags = $vm.DiagnosticsProfile.BootDiagnostics
if ($bootDiags.Enabled -eq $true) {
Write-Host "✓ Boot diagnostics enabled on $($vm.Name)" -ForegroundColor Green
Write-Host " Storage URI: $($bootDiags.StorageUri)"
} else {
Write-Host "✗ Boot diagnostics not enabled on $($vm.Name)" -ForegroundColor Red
}
KQL Query: Find VMs Without Boot Diagnostics
Use this Azure Resource Graph query to identify VMs that don't have Serial Console access configured:
Resources
| where type == "microsoft.compute/virtualmachines"
| extend bootDiagsEnabled = properties.diagnosticsProfile.bootDiagnostics.enabled
| extend storageUri = properties.diagnosticsProfile.bootDiagnostics.storageUri
| where bootDiagsEnabled != true or isnull(bootDiagsEnabled)
| project
vmName = name,
resourceGroup,
location,
powerState = properties.extended.instanceView.powerState.displayStatus,
bootDiagsEnabled,
storageUri,
subscriptionId
| order by vmName asc
What this query finds:
- VMs with boot diagnostics disabled
- VMs where boot diagnostics was never configured
- The storage account used (or missing)
- Current power state of VMs
Output example:
vmName resourceGroup location powerState bootDiagsEnabled storageUri
vm-app-001 rg-prod-001 eastus VM running false null
vm-db-002 rg-prod-002 westus2 VM running null null
vm-web-003 rg-test-001 eastus VM deallocated false null
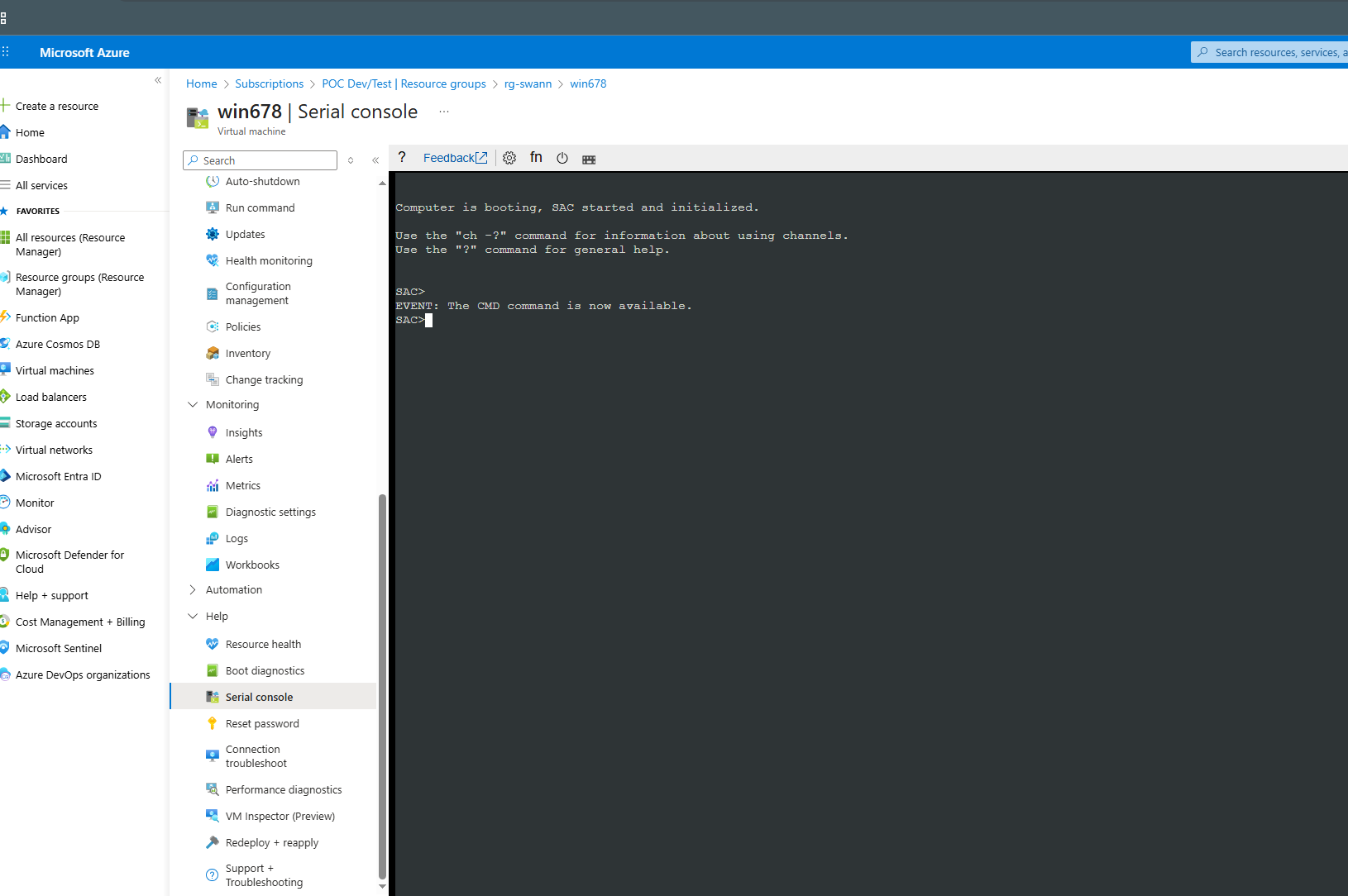
Using Serial Console: Windows VMs
Accessing Windows Serial Console
- Navigate to: VM → Help → Boot diagnostics → Serial console
- Wait for connection (5-10 seconds)
- You'll see the SAC prompt:
SAC>
If you see a blank screen, press ESC + TAB to activate SAC.
Windows SAC (Special Administration Console) Commands
# List all available SAC commands
SAC> ?
# Create a CMD channel
SAC> cmd
# Output: "The Command Prompt session was successfully launched."
# Output: "Channel: Cmd0001"
# Switch to CMD channel (use channel name from output)
SAC> ch -sn Cmd0001
# Or use shortcut: ESC + TAB to switch channels
# Press Enter to see login prompt
# Login with VM credentials
# Domain: (leave blank for local account)
# Username: azureadmin
# Password: ********
Common Windows Troubleshooting Commands
Once logged into the CMD channel, you can run standard Windows commands:
# Check network configuration
ipconfig /all
# Verify DNS resolution
nslookup microsoft.com
# Test network connectivity
ping 8.8.8.8
# Check firewall status
netsh advfirewall show allprofiles
# View network connections
netstat -an | more
# Check for open ports
netstat -ano | findstr :3389
# Reset admin password (if locked out)
net user azureadmin NewP@ssw0rd!
# Unlock locked account
net user azureadmin /active:yes
# Check disk space
dir c:\
wmic logicaldisk get caption,freespace,size
# View running services
sc query | more
# Restart specific service
sc stop "ServiceName"
sc start "ServiceName"
# Check boot configuration
bcdedit /enum
# Boot to safe mode (for next restart only)
bcdedit /set {default} safeboot minimal
# Remove safe mode flag (after fixing issue)
bcdedit /deletevalue {default} safeboot
# View recent event logs (last 10 errors)
wevtutil qe System /c:10 /rd:true /f:text /q:"*[System[(Level=2)]]"
# Start PowerShell from CMD
powershell
PowerShell Commands in SAC
After typing powershell in the CMD channel:
# Check RDP configuration
Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections"
# Enable RDP if disabled
Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections" -Value 0
# Check Windows Firewall rules for RDP
Get-NetFirewallRule -DisplayName "Remote Desktop*" | Select-Object DisplayName, Enabled
# Check if Windows Update service is running
Get-Service -Name wuauserv
# View installed Windows Updates (last 10)
Get-HotFix | Sort-Object InstalledOn -Descending | Select-Object -First 10
# Check for pending reboots
Test-Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Component Based Servicing\RebootPending"
Test-Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\RebootRequired"
SAC Limitations and Workarounds
SAC runs in 80x24 character mode:
- No scrollback buffer
- Add | more to long outputs
- Use PowerShell for better formatting
No GUI access:
- Can't launch graphical tools
- Use command-line equivalents
- Consider offline disk repair for complex GUI issues
Session timeout:
- Default: No automatic timeout (Windows)
- Manually disconnect when finished
- Other users can forcefully disconnect you
Using Serial Console: Linux VMs
Accessing Linux Serial Console
- Navigate to: VM → Help → Boot diagnostics → Serial console
- Wait for connection
- Press Enter to see login prompt
- Login with VM credentials
Common Linux Troubleshooting Commands
# Check network configuration
ip addr show
ip route show
# View DNS configuration
cat /etc/resolv.conf
# Test network connectivity
ping -c 4 8.8.8.8
# Check if SSH is running
systemctl status sshd
# Restart SSH service
sudo systemctl restart sshd
# View recent system logs
sudo journalctl -xb -n 50
# Check disk usage
df -h
# Check memory usage
free -h
# View running processes
ps aux | head -20
# Check open ports
sudo netstat -tulpn
# View firewall rules (if firewalld)
sudo firewall-cmd --list-all
# View firewall rules (if ufw)
sudo ufw status verbose
# View failed login attempts
sudo lastb | head -20
# Check for filesystem errors
sudo dmesg | grep -i error
# View boot messages
sudo journalctl -b
# Check SELinux status (if enabled)
getenforce
# Temporarily disable SELinux (troubleshooting only)
sudo setenforce 0
Resetting Root Password (Emergency Access)
If you've lost root access and have physical console access:
- Interrupt boot process:
- Reboot VM via Azure Portal
- In Serial Console, press any key when GRUB menu appears
-
Press
eto edit boot parameters -
Modify kernel parameters:
```bash
# Find line starting with "linux" or "linux16"
# At the end of that line, add:
init=/bin/bash
# Press Ctrl+X or F10 to boot
```
- Remount filesystem and reset password:
```bash
# Remount root filesystem as read-write
mount -o remount,rw /
# Reset root password
passwd root
# Enter new password twice
# Remount as read-only
mount -o remount,ro /
# Force reboot
echo b > /proc/sysrq-trigger
```
Fixing Network Configuration
# Restart networking (Ubuntu/Debian)
sudo systemctl restart networking
# Restart networking (RHEL/CentOS)
sudo systemctl restart network
# View network interfaces
ip link show
# Bring interface up
sudo ip link set eth0 up
# Check DHCP client
sudo systemctl status dhclient
# Release and renew DHCP lease
sudo dhclient -r eth0
sudo dhclient eth0
# View routing table
ip route show
# Add default route (if missing)
sudo ip route add default via 10.0.0.1 dev eth0
Checking Azure Guest Agent
# Check if Azure Guest Agent (waagent) is running
sudo systemctl status walinuxagent
# Restart Azure Guest Agent
sudo systemctl restart walinuxagent
# View Azure Guest Agent logs
sudo cat /var/log/waagent.log | tail -50
Real Scenarios: When You Need Serial Console
Scenario 1: VM Won't Boot After Windows Update
Problem:
- Applied Windows Updates
- VM restarted but never came back online
- Can't RDP, connection times out
- Azure Portal shows VM as "Running"
Solution via Serial Console:
SAC> cmd
SAC> ch -sn Cmd0001
[Press Enter]
[Login with credentials]
# Check boot configuration
bcdedit /enum
# View Windows Update logs
dir C:\Windows\Logs\WindowsUpdate
# Boot to safe mode
bcdedit /set {default} safeboot minimal
# Restart VM
shutdown /r /t 0
After VM restarts in safe mode:
- Uninstall problematic update via Control Panel
- Remove safe mode flag: bcdedit /deletevalue {default} safeboot
- Restart normally
Scenario 2: Firewall Misconfiguration Locked You Out
Problem:
- Modified NSG rules or Windows Firewall
- Accidentally blocked RDP/SSH access
- Can't connect to fix it
Solution via Serial Console (Windows):
# Check Windows Firewall status
netsh advfirewall show allprofiles
# Temporarily disable Windows Firewall
netsh advfirewall set allprofiles state off
# Check if RDP is listening
netstat -an | findstr :3389
# Enable RDP via registry
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
Solution via Serial Console (Linux):
# Check firewall status
sudo iptables -L -n
# Flush all firewall rules (temporary)
sudo iptables -F
# Or disable firewalld
sudo systemctl stop firewalld
# Verify SSH is running
sudo systemctl status sshd
# Check SSH configuration
sudo sshd -T | grep -i permitroot
Scenario 3: Static IP Configuration Broke Networking
Problem:
- Someone configured static IP in guest OS (big mistake in Azure)
- VM lost network connectivity
- Azure expects DHCP for IP assignment
Solution via Serial Console (Windows):
# View current IP configuration
ipconfig /all
# Set network adapter back to DHCP
netsh interface ip set address "Ethernet" dhcp
netsh interface ip set dnsservers "Ethernet" dhcp
# Release and renew DHCP
ipconfig /release
ipconfig /renew
# Verify connectivity
ping 8.8.8.8
Solution via Serial Console (Linux):
# Edit network configuration file
sudo vi /etc/netplan/50-cloud-init.yaml
# Change to DHCP (for Ubuntu 18.04+):
# network:
# version: 2
# ethernets:
# eth0:
# dhcp4: true
# Apply changes
sudo netplan apply
# Verify
ip addr show eth0
Scenario 4: Locked Admin Account (Too Many Failed Logins)
Problem:
- Account locked after too many failed RDP/SSH attempts
- Can't login to unlock it
Solution via Serial Console (Windows):
# Check account status
net user azureadmin
# Unlock account
net user azureadmin /active:yes
# Reset password (if needed)
net user azureadmin NewP@ssw0rd!
# Verify account unlocked
net user azureadmin
Solution via Serial Console (Linux):
# Unlock user account
sudo pam_tally2 --user=azureadmin --reset
# Or for newer systems using faillock
sudo faillock --user azureadmin --reset
# Verify user can login
sudo passwd azureadmin
Scenario 5: Azure Guest Agent Crashed
Problem:
- Azure Guest Agent (waagent) stopped responding
- Portal shows "Not Ready" status
- Can't execute Run Commands or extensions
Solution via Serial Console (Linux):
# Check agent status
sudo systemctl status walinuxagent
# View recent logs
sudo journalctl -u walinuxagent -n 100
# Restart agent
sudo systemctl restart walinuxagent
# Check if agent started successfully
sudo systemctl status walinuxagent
# View agent version
waagent -version
Troubleshooting Serial Console
"Serial Console Not Available for This VM"
Possible causes:
- Boot diagnostics not enabled
```powershell
# Check status
$vm = Get-AzVM -ResourceGroupName "rg-prod" -Name "vm-app-001"
$vm.DiagnosticsProfile.BootDiagnostics.Enabled
# Enable it
Set-AzVMBootDiagnostic -VM $vm -Enable -ResourceGroupName "rg-shared" -StorageAccountName "saproddiag001"
Update-AzVM -VM $vm -ResourceGroupName "rg-prod"
```
- Serial Console disabled at subscription level
```powershell
# Check feature status
Get-AzProviderFeature -FeatureName "EnableSerialConsole" -ProviderNamespace "Microsoft.SerialConsole"
# Enable if not registered
Register-AzProviderFeature -FeatureName "EnableSerialConsole" -ProviderNamespace "Microsoft.SerialConsole"
```
- VM is deallocated (not running)
- Serial Console only works on running VMs
- Start the VM first
"Cannot Connect to Serial Console"
Windows (SAC not responding):
- Press ESC + TAB to activate SAC
- If still blank, SAC might not be configured
- Check if EMS is enabled:
```powershell
# Via Run Command (if available)
Get-Service EMS
# Enable EMS via offline disk repair if needed
bcdedit /ems {default} on
bcdedit /emssettings EMSPORT:1 EMSBAUDRATE:115200
```
Linux (no login prompt):
- Press Enter multiple times
- Check if console is configured in GRUB:
```bash
# Via SSH or Run Command if available
cat /etc/default/grub | grep console
# Should include: console=ttyS0,115200n8
```
- Regenerate GRUB configuration:
```bash
# Ubuntu/Debian
sudo update-grub
# RHEL/CentOS
sudo grub2-mkconfig -o /boot/grub2/grub.cfg
```
Storage Account Firewall Blocking Access
Error: "Web socket is closed or could not be opened"
Cause: Boot diagnostics storage account has firewall enabled, blocking Azure Serial Console service
Solution:
# Option 1: Switch to managed boot diagnostics (recommended)
$vm = Get-AzVM -ResourceGroupName "rg-prod" -Name "vm-app-001"
Set-AzVMBootDiagnostic -VM $vm -Enable
Update-AzVM -VM $vm -ResourceGroupName "rg-prod"
# Option 2: Add Serial Console service IPs to storage account firewall
# Navigate to storage account → Networking → Firewall
# Add IP ranges based on VM region:
# - East US: 52.186.138.80/29
# - West US: 52.250.65.160/29
# - See Microsoft docs for full list by region
Insufficient Permissions
Error: "You do not have permission to access serial console"
Required role: Virtual Machine Contributor or higher
# Check current role assignments
Get-AzRoleAssignment -ObjectId <your-user-object-id> -ResourceGroupName "rg-prod"
# Grant access (by subscription owner)
New-AzRoleAssignment -ObjectId <user-object-id> `
-RoleDefinitionName "Virtual Machine Contributor" `
-ResourceGroupName "rg-prod"
When Serial Console Doesn't Help
Be honest: Serial Console isn't magic. Here's when it won't save you:
Disk Corruption
Problem:
- Filesystem corruption
- Missing boot files
- Damaged disk
Why Serial Console doesn't help:
- Can't repair filesystem while OS is using it
- Boot loader corruption prevents even console access
Solution: Offline disk repair
# Attach OS disk to rescue VM
$disk = Get-AzDisk -ResourceGroupName "rg-prod" -DiskName "vm-app-001_OsDisk"
$rescueVM = Get-AzVM -ResourceGroupName "rg-prod" -Name "vm-rescue-001"
Add-AzVMDataDisk -VM $rescueVM `
-Name "broken-os-disk" `
-ManagedDiskId $disk.Id `
-Lun 1 `
-CreateOption Attach
Update-AzVM -VM $rescueVM -ResourceGroupName "rg-prod"
# Now RDP to rescue VM and repair disk as data disk
# Use chkdsk (Windows) or fsck (Linux)
Complete Boot Failure (Kernel Panic/BSOD Loop)
Problem:
- VM crashes during boot
- Kernel panic (Linux) or BSOD (Windows)
- Never reaches point where Serial Console can help
Why Serial Console doesn't help:
- OS never loads enough to accept console input
- Can see boot messages but can't interact
Solution: Boot diagnostics screenshot + offline repair
# View boot diagnostics screenshot
$vm = Get-AzVM -ResourceGroupName "rg-prod" -Name "vm-app-001"
$vm.DiagnosticsProfile.BootDiagnostics.ConsoleScreenshotBlobUri
# Screenshot shows error message but can't fix interactively
# Must use offline disk repair or redeploy VM
Performance Issues
Problem:
- VM is slow
- High CPU usage
- Memory exhaustion
Why Serial Console isn't ideal:
- Text-only interface is slow for performance troubleshooting
- Better tools available (Azure Monitor, VM Insights)
Better solution:
# Use Azure Monitor metrics
Get-AzMetric -ResourceId $vm.Id -MetricName "Percentage CPU" -TimeGrain 00:05:00
# Or install Azure Monitor Agent for detailed insights
# (NOW you install AMA - for monitoring, not console access)
Complex GUI-Required Tasks
Problem:
- Need to use graphical tools
- Registry Editor with visual navigation
- Disk Management GUI
Why Serial Console doesn't help:
- Command-line only
- No graphics support
Workaround: Use Azure Bastion or RDP if networking works, or offline disk repair
The Real Lesson: Azure Isn't Missing VMware Features
Azure doesn't lack features VMware has—the features are just hidden in weird places.
Feature Comparison
| VMware Feature | Azure Equivalent | Where to Find It |
|---|---|---|
| VM Console | Serial Console | Help → Boot Diagnostics → Serial Console |
| Console Screenshots | Boot Diagnostics | Help → Boot Diagnostics (screenshot updated every 60s) |
| Remote Access | Azure Bastion | VM → Connect → Bastion |
| Power Management | Portal Controls | VM → Overview → Start/Stop/Restart |
| Performance Monitoring | Azure Monitor | VM → Monitoring → Metrics |
What VMware admins need to know:
1. Stop clicking "Connect" expecting VMware console behavior
2. Bookmark: VM → Help → Boot diagnostics → Serial console
3. Enable Serial Console at subscription level before emergencies
4. Learn SAC commands (Windows) or GRUB escape (Linux)
5. Don't install AMA thinking you need it for console access
The Real VMware → Azure Translation
VMware thinking:
"I need console access, let me click the console button"
Azure reality:
"There are two different features:
- Connect button = daily remote access (Bastion/RDP/SSH)
- Serial Console = emergency troubleshooting (buried in Help menu)"
VMware thinking:
"Console access must require some agent or extension"
Azure reality:
"Serial Console is hypervisor-level, no agent needed. AMA is for monitoring, not console."
Quick Reference Card
Save this for your team:
╔═══════════════════════════════════════════════════════════════╗
║ AZURE SERIAL CONSOLE - QUICK REFERENCE ║
╠═══════════════════════════════════════════════════════════════╣
║ Where? VM → Help → Boot Diagnostics → Serial Console ║
║ Requires? Boot diagnostics enabled, VM running, subscription ║
║ feature enabled. NO AMA NEEDED. ║
╠═══════════════════════════════════════════════════════════════╣
║ WINDOWS (SAC) ║
║ SAC> cmd Create CMD channel ║
║ SAC> ch -sn Cmd0001 Switch to channel ║
║ ESC+TAB Activate SAC or switch channels ║
║ ipconfig /all Network info ║
║ bcdedit /enum Boot config ║
╠═══════════════════════════════════════════════════════════════╣
║ LINUX ║
║ [Press Enter] Show login prompt ║
║ ip addr show Network config ║
║ sudo journalctl -xb Boot logs ║
║ systemctl status sshd Check SSH ║
╠═══════════════════════════════════════════════════════════════╣
║ WHEN TO USE ║
║ ✓ Can't RDP/SSH (network broken) ║
║ ✓ VM won't boot (see boot messages) ║
║ ✓ Locked account (reset password via SAC) ║
║ ✓ Firewall misconfiguration (fix from inside) ║
╠═══════════════════════════════════════════════════════════════╣
║ WHEN IT DOESN'T HELP ║
║ ✗ Disk corruption (use offline repair) ║
║ ✗ Complete boot failure (attach disk to rescue VM) ║
║ ✗ Performance issues (use Azure Monitor) ║
╚═══════════════════════════════════════════════════════════════╝
Summary: Stop Clicking the Wrong Button
If you take nothing else away from this post:
-
The "Connect" button is not console access - it's Bastion/RDP/SSH (requires networking)
-
Serial Console is the real console - hypervisor-level access in Help → Boot Diagnostics
-
You don't need Azure Monitor Agent for console access - Serial Console works without any agents
-
Enable Serial Console now, before you need it in an emergency
-
Learn the SAC commands (Windows) or basic Linux troubleshooting commands
-
Keep offline disk repair in your back pocket for when Serial Console can't help
Azure has the features VMware admins need. Microsoft just hid them in weird places and gave them confusing names. Now you know where to look.
Next time someone on your team says: "Azure doesn't have a console like VMware"
Send them here. They're just clicking the wrong button.
Additional Resources
Microsoft Official Docs:
- Serial Console for Windows VMs
- Serial Console for Linux VMs
- Enable/Disable Serial Console
PowerShell Scripts:
- Enable boot diagnostics at scale (see Step 4 above)
- KQL query to find VMs without boot diagnostics (see above)
Related Post Ideas:
- Offline disk repair in Azure (for when Serial Console fails)
- Azure Bastion vs Serial Console vs RDP (when to use each)
- Common Azure migration gotchas for VMware admins
Have questions about Serial Console or other Azure operational topics? Let me know in the comments or reach out via the contact form.
