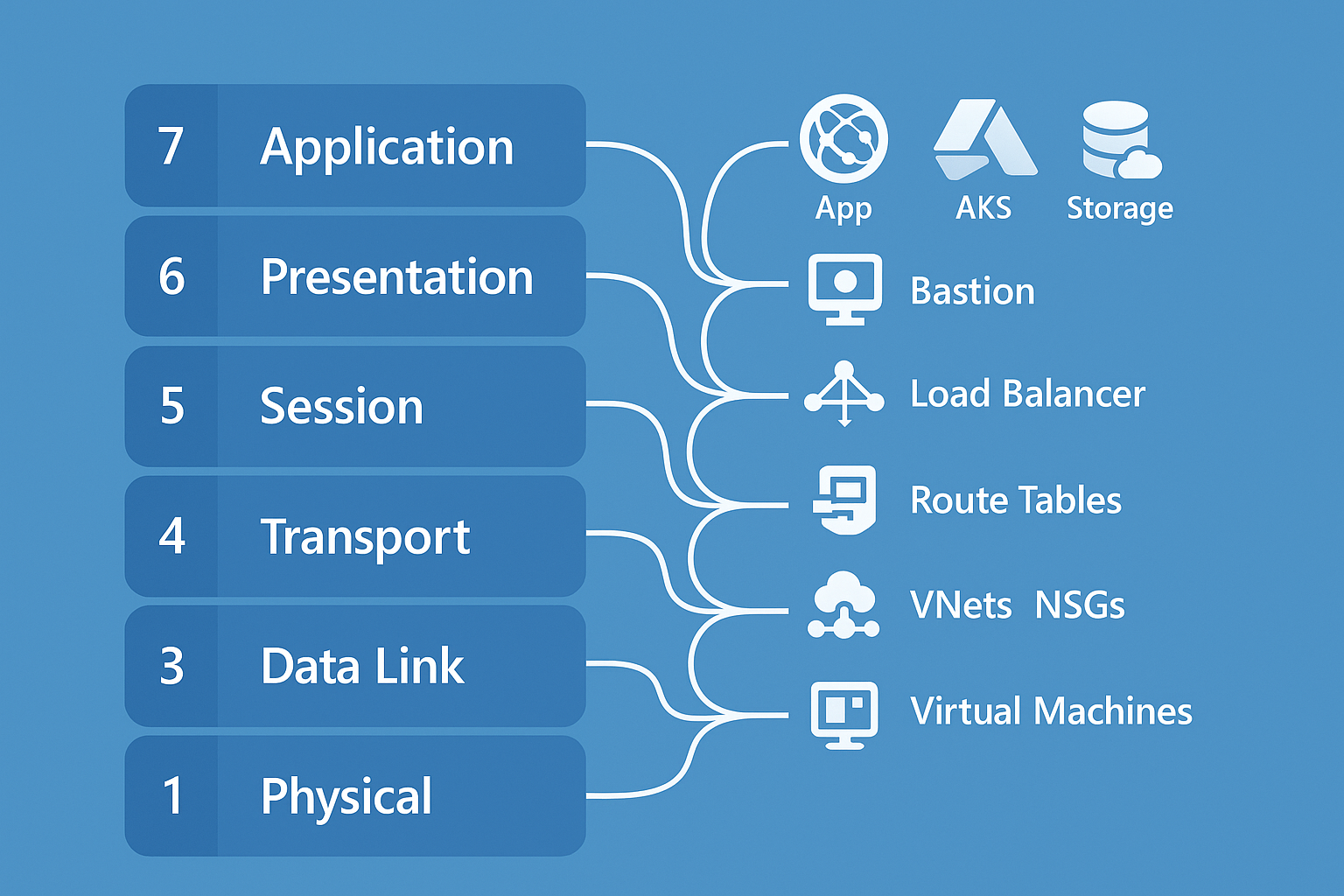
The OSI Model for Azure Admins: How to Troubleshoot the Cloud Like a Network Engineer
2025-11-03 · ~6 min read
The OSI model isn’t dead — it just moved to the cloud. Here’s how to map Azure services to OSI layers and use that framework to troubleshoot IaaS, PaaS, and SaaS workloads efficiently.
This guide is part of our Azure Automation hub covering Infrastructure as Code, CI/CD pipelines, and DevOps practices.
🧭 Introduction
The OSI model (Open Systems Interconnection) is still one of the best mental maps for troubleshooting networks — even in the cloud.
In Azure, every issue — from a VM that won’t ping to an App Service failing to load — lives somewhere on those seven layers.
If you can pinpoint the layer, you can pinpoint the problem.
This guide maps Azure’s IaaS, PaaS, and SaaS services directly to the OSI model and shows how to use that structure to troubleshoot modern cloud environments.
🔷 Layer 1 — Physical: The Azure Fabric
Concept: Hardware, cabling, physical connectivity
Azure Reality: The physical hosts, SDN fabric, and storage managed by Microsoft
Services:
- Virtual Machines (compute hosts)
- Managed Disks
- App Service Plan compute (abstracted)
- Azure Stack Hub (on-prem hybrid)
Troubleshooting:
- Check Azure Service Health for regional outages
- Check Resource Health on VMs or disks
- Review Maintenance events or host reallocation logs
🔷 Layer 2 — Data Link: Virtual Network Isolation
Concept: MAC addressing, switching, local delivery
Azure Reality: VNets, subnets, NSGs, and Private Endpoints form layer-2 boundaries
Services:
- VNets / Subnets
- Network Interfaces (NICs)
- NSGs
- Private Endpoints & Service Endpoints
- App Service Environment (ASE)
Troubleshooting:
- Use Network Watcher → IP Flow Verify
- Check Effective Security Rules for NSGs
- Validate Private Endpoint DNS mapping and status
🔷 Layer 3 — Network: Routing & Addressing
Concept: IP routing and path selection
Azure Reality: Virtual routers and firewalls manage IP movement between VNets and regions
Services:
- Route Tables (UDRs)
- VNet Peering
- VPN Gateway / Virtual WAN / ExpressRoute
- Azure Firewall
- Azure DNS
- Storage Accounts (via Service/Private Endpoints)
Troubleshooting:
- Review Effective Routes on VM NICs
- Use Network Watcher → Next Hop
- Check for overlapping IP spaces or missing routes
- Validate DNS resolution for storage or service endpoints
🔷 Layer 4 — Transport: Ports & Load Balancing
Concept: TCP/UDP sessions and port control
Azure Reality: Load balancers, firewalls, and NSGs enforce connectivity at this layer
Services:
- Azure Load Balancer (L4)
- Azure Firewall
- NSGs
- Storage Accounts (TCP 443 HTTPS / 445 SMB)
- App Service inbound ports (80/443)
- AKS node networking
Troubleshooting:
- Run Test-NetConnection <fqdn> -Port 443
- Verify NSG Flow Logs
- Check Load Balancer health probes
- Confirm firewall and NVA NAT rules
🔷 Layer 5 — Session: Identity & Persistence
Concept: Establishing and maintaining sessions
Azure Reality: Authentication, tokens, and session lifetimes managed by Entra ID or SAS tokens
Services:
- Azure Bastion / Jumpboxes (RDP, SSH)
- Entra ID (Azure AD)
- App Service / Functions with AD authentication
- Storage Accounts (SAS, RBAC)
- SQL / Cosmos DB (token or connection string auth)
- API Management (session affinity)
Troubleshooting:
- Review Sign-in logs in Entra ID
- Check token expiry or refresh failures
- Validate RBAC or SAS permissions
- Ensure sticky sessions are configured if required
🔷 Layer 6 — Presentation: Encryption & Format
Concept: Data encryption, serialization, translation
Azure Reality: TLS, Key Vault, and encryption at rest or in transit
Services:
- Azure Key Vault (certificates, secrets)
- Application Gateway / Front Door (TLS offload)
- Storage (SSE, CMK)
- SQL Database (TDE)
- API Management (policy transforms)
- Functions / Web Apps (HTTPS endpoints)
Troubleshooting:
- Check TLS version and SSL certificate expiry
- Validate Key Vault access policies
- Review SSL policy on App Gateway
- Confirm encryption configuration in Storage or SQL
🔷 Layer 7 — Application: Apps, APIs & Data Services
Concept: End-user and application-level communication
Azure Reality: Where workloads and user experiences live
Services:
- IaaS: IIS / NGINX / Custom web apps on VMs
- PaaS:
- App Service
- Functions (serverless)
- AKS / Container Apps
- Logic Apps
- API Management
- Application Gateway (WAF)
- Storage Blob / Queue / Table APIs
- SQL Database / Cosmos DB
- SaaS: Microsoft 365, Dynamics 365, Power BI
Troubleshooting:
- Use Application Insights to trace requests and dependencies
- Run App Service Diagnostics → Availability & Performance
- Check Front Door or App Gateway WAF logs
- Review API exceptions and HTTP codes (403, 409)
- Validate DNS and endpoint reachability
🧩 Layer-to-Service Mapping Table
| OSI Layer | Focus | Example Azure Services | Key Troubleshooting Tools |
|---|---|---|---|
| 1 – Physical | Compute & Fabric | VMs, Disks, App Service Plan | Service Health, Resource Health |
| 2 – Data Link | Network Isolation | VNets, Subnets, NSGs, Private Endpoints | IP Flow Verify, Effective Rules |
| 3 – Network | Routing & DNS | Route Tables, VPN, Firewall, Storage (PE), DNS | Next Hop, Connection Monitor |
| 4 – Transport | Ports & Load Balancing | LB, NSG, Firewall, App Svc Ports, Storage (443/445) | Test-NetConnection, Flow Logs |
| 5 – Session | Identity & Tokens | Bastion, Entra ID, Storage SAS, SQL Auth | Sign-in Logs, Token Trace |
| 6 – Presentation | Encryption & Format | Key Vault, App GW, Front Door, Storage SSE, SQL TDE | SSL Logs, Cert Expiry, TLS Checks |
| 7 – Application | Apps & APIs | App Service, AKS, Functions, Logic Apps, SQL, Storage API | App Insights, Diagnostics, WAF Logs |
⚙️ Applying the OSI Model in Real Troubleshooting
When something breaks — start low, climb up.
Example: A VM can’t access a Storage Account
1. Layer 3: Check VNet routes and Private Endpoint connectivity
2. Layer 4: Verify port 443 open in NSG or Firewall
3. Layer 5: Validate SAS token or AD permissions
4. Layer 6: Confirm TLS handshake / cert expiry
5. Layer 7: Review app logs and Storage API responses
Example: App Service can’t reach SQL Database
- Start with DNS & VNet integration (L3)
- Check port 1433 (L4)
- Verify managed identity (L5)
- Review SSL policy (L6)
- Inspect query errors (L7)
🧠 Key Takeaways
- The OSI model is a cloud-agnostic troubleshooting map.
- Azure’s layers stack cleanly across IaaS, PaaS, and SaaS.
- Starting from the bottom prevents chasing phantom “app” issues caused by simple network misconfigurations.
🖼️ Hero Image Prompt
“An Azure-blue layered diagram of the 7-layer OSI model on the left, matched with Azure icons and services (VMs, VNets, NSGs, Route Tables, Firewall, Key Vault, App Service, AKS, Functions, Storage, SQL, and Front Door) on the right, connected with curved data-flow lines.”
💬 Final Thought
The next time your app “just stops working,” don’t panic — walk the stack.
Layer 1: Is Azure itself healthy?
Layer 2–3: Is the network open?
Layer 4–6: Is the path secure and the session valid?
Layer 7: Is your app behaving?
Master these seven questions, and you’ll troubleshoot Azure like a pro.
Published by Azure-Noob — practical cloud ops for real admins.
Azure Admin Starter Kit (Free Download)
Get my KQL cheat sheet, 50 Windows + 50 Linux commands, and an Azure RACI template in one free bundle.
Get the Starter Kit →Get Azure operational guides in your inbox
Weekly tips from managing 44 Azure subscriptions. No marketing BS.
Join 500+ Azure admins. Unsubscribe anytime.
