What I Wish I Knew About Azure Resource Tags
2025-09-23 · ~9 min read
Order, capitalization, spelling, and the Type tag that will save your sanity. Hard-earned lessons from real Azure environments.
What I Wish I Knew About Azure Resource Tags
Before you deploy your first resource, read this. Before you write your first cost report, definitely read this.
Azure resource tags seem simple: key-value pairs that help organize resources. The Azure documentation makes it sound straightforward. Reality? Tags are the difference between having clean cost reports and spending your weekend manually sorting through billing chaos.
Here's what I learned the hard way.
The "We'll Tag Later" Trap
The mistake: Deploying resources first, planning tags second.
The reality: You'll never go back and tag everything properly. That VM deployed for "quick testing" will be running in production six months later with zero tags, and you'll have no idea which department to bill.
What I do now: Tag standards come before the first resource group. Non-negotiable.
Order, Capitalization, and Spelling: The Holy Trinity of Tag Discipline
These three things will make or break your tagging strategy:
Capitalization Consistency
Tags are case-sensitive. That means:
- Environment: prod
- Environment: Prod
- Environment: PROD
Are three different tags. Your cost reports will split production costs across three categories, and your CFO will ask uncomfortable questions.
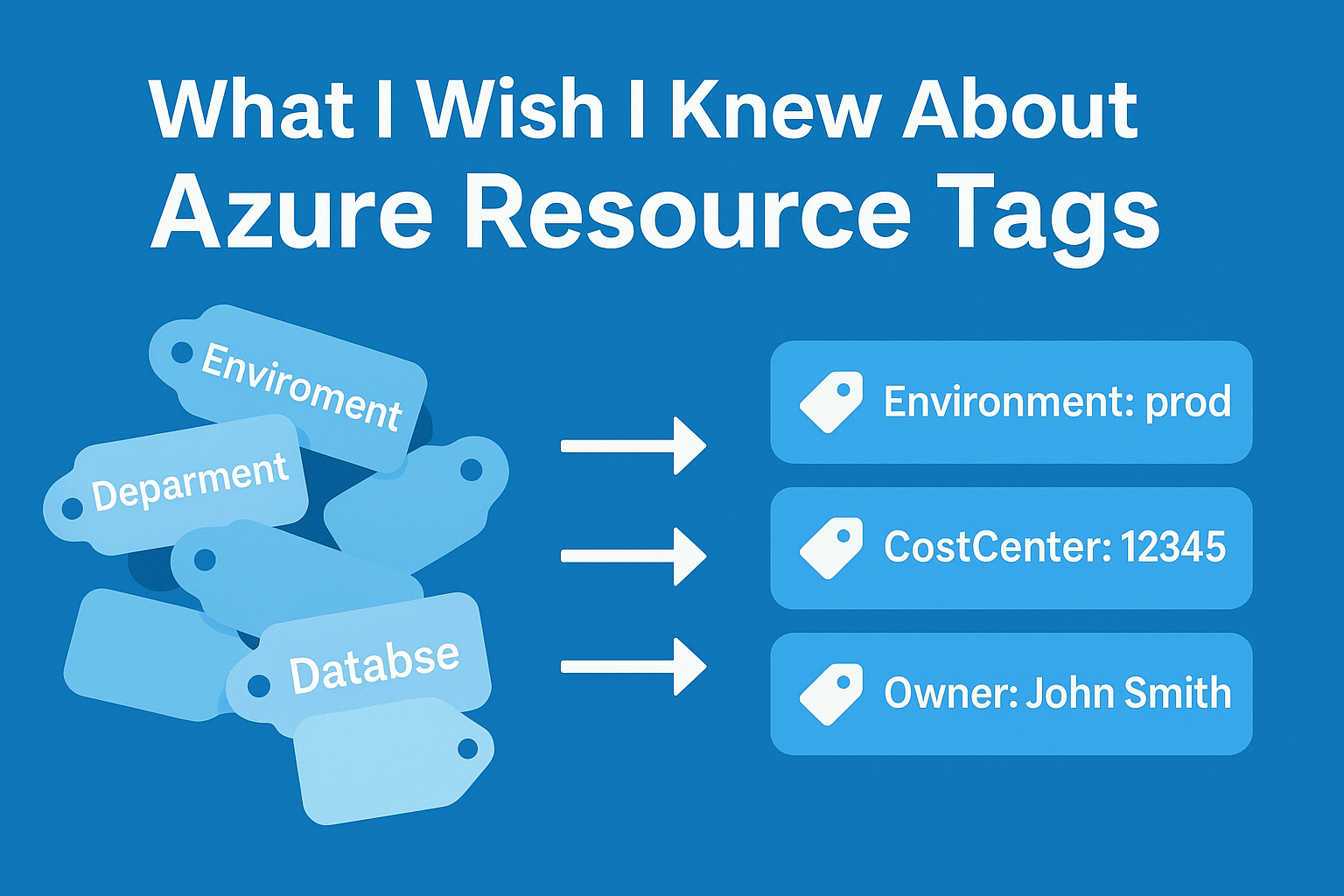
Spelling: One Typo Breaks Everything
Enviroment vs Environment. Databse vs Database. Appliction vs Application.
Every spelling variation creates a separate tag category:
- Your cost reports split across multiple categories
- Compliance queries miss misspelled resources
- Automation scripts fail to find resources
- Policy exemptions don't apply
Common spelling disasters I've seen:
- Enviroment (missing 'n')
- Databse (missing 'a')
- Appliction (missing 'a')
- Deparment (missing 't')
- Maintainance (should be 'Maintenance')
One misspelled tag in production can take weeks to clean up because you have to identify every affected resource and update tags individually.
Alphabetical Order Matters
Define your tag order and stick to it. When you're looking at hundreds of resources, consistent ordering prevents mistakes:
Application: customer-portal
CostCenter: 12345
Department: engineering
Environment: prod
Owner: john.smith
Type: Server
Enforce with Azure Policy: Manual compliance doesn't work. Use Azure Policy to enforce exact spelling, capitalization, and allowed values.
The Required vs. Optional Tag Strategy
Required tags (enforced via Azure Policy):
- CostCenter - For chargeback
- Owner - Who to call at 3 AM
- Environment - prod/dev/test for governance
- Department - Business unit accountability
- Type - Resource classification (critical for operations)
The Type Tag: You'll Thank Me Later
This is the most important tag you're not using:
Type: Server - Production workloads, patching schedules, backup requirements
Type: Desktop - VDI, different lifecycle, user-focused policies
Type: Appliance - Network devices, specialized maintenance windows
Type: Databricks - Data platform, different scaling and cost patterns
Why Type matters:
- Patching strategies: Servers vs Desktops have different update schedules
- Cost allocation: Databricks clusters cost differently than traditional VMs
- Lifecycle management: Appliances follow vendor support cycles
- Security policies: Each type needs different hardening approaches
Your KQL queries become infinitely more useful when you can filter by Type:
Resources
| where type == "microsoft.compute/virtualmachines"
| extend ResourceType = tostring(tags["Type"])
| where ResourceType == "Server"
| summarize count() by tostring(tags["Environment"])
Optional but valuable:
- Application - Groups related resources
- Project - Temporary initiatives
- MaintenanceWindow - When can we patch this?
- DataClassification - Security and compliance
The key insight: Start with 4-5 required tags maximum. You can always add more, but you can't force retroactive compliance on 500 untagged resources.
Tag Inheritance Doesn't Work Like You Think
Resource Groups pass tags to resources, but only at creation time. If you update the Resource Group tags later, existing resources keep their old tags.
This breaks cost allocation: Your new tagging strategy won't apply to existing resources until you manually update them.
Solution: Use Azure Resource Graph to find untagged resources and bulk-update them.
Resources
| where tags !has "CostCenter"
| project name, resourceGroup, type, tags
| limit 100
Tag Limits Are Real and Painful
- 15 tags per resource maximum
- 512 characters per tag name
- 256 characters per tag value
Hit the 15-tag limit once and you'll understand why tag planning matters. I've seen teams try to cram everything into tags and hit the wall when they need one more for compliance.
My rule: Reserve 3-4 tag slots for future requirements. Don't use all 15 on day one.
The Empty Tag Problem
This query from my VM inventory shows the issue:
CostCenter = tostring(tags["CostCenter"]),
Owner = tostring(tags["Owner"])
If the tag doesn't exist, you get empty cells in your report. Finance sees blank cost centers and assumes it's a data problem.
Better approach: Provide defaults in your queries.
CostCenter = iif(isempty(tags["CostCenter"]), "Unassigned", tostring(tags["CostCenter"]))
Azure Policy: The Only Way Tag Governance Actually Works
Manual tagging doesn't scale. Period. You need Azure Policy to enforce your standards, or you'll be chasing tag compliance forever.
Required tag policies that prevent deployment without proper tags:
{
"if": {
"field": "tags['CostCenter']",
"exists": "false"
},
"then": {
"effect": "deny"
}
}
Allowed values policies that prevent typos and variations:
{
"if": {
"allOf": [
{
"field": "tags['Environment']",
"exists": "true"
},
{
"field": "tags['Environment']",
"notIn": ["prod", "dev", "test"]
}
]
},
"then": {
"effect": "deny"
}
}
Automatic value policies for Type tag:
// If VM size starts with "Standard_D", auto-tag as Type: Server
// If in VDI resource group, auto-tag as Type: Desktop
// If resource name contains "databricks", auto-tag as Type: Databricks
Without Azure Policy: Someone will deploy resources with Environemnt: Production and break your reporting.
With Azure Policy: Deployment fails immediately with a clear error message.
The key insight: Policy errors during deployment are infinitely better than silent tag compliance failures discovered during month-end reporting.
Cost Allocation Reality Check
Tags enable chargeback, but only if you plan for it:
This works:
- CostCenter: 12345 (maps to finance system)
- Department: engineering (matches org chart)
- Project: customer-portal (has a budget)
This doesn't work:
- Owner: john (John left the company)
- Purpose: testing (too vague for billing)
- Temporary: yes (running for 8 months now)
The Tag Governance Framework
Month 1: Define 4-5 core tags, implement via Azure Policy
Month 3: Audit compliance, clean up violations
Month 6: Add specialized tags for specific teams
Month 12: Review and optimize based on actual usage
Common failure: Trying to design the perfect tagging system upfront. Start simple, iterate based on real reporting needs.
Practical Tag Queries for Operations
Find untagged resources:
Resources
| where isnull(tags) or array_length(todynamic(tostring(tags))) == 0
| project name, resourceGroup, type, location
Cost center compliance check:
Resources
| extend CostCenter = tags["CostCenter"]
| where isempty(CostCenter)
| summarize UntaggedResources = count() by resourceGroup
Tag standardization audit:
Resources
| extend Environment = tags["Environment"]
| where isnotempty(Environment)
| summarize count() by Environment
// Look for variations: prod, Prod, PROD, production
What I'd Do Differently
- Start with cost allocation requirements, not technical categorization
- Enforce tag standards from day one via Azure Policy
- Build tag compliance into deployment pipelines
- Plan for tag evolution - leave room for future requirements
- Train teams on tag business impact - this isn't just metadata
The Bottom Line
Tags aren't technical metadata - they're business process enablers. Get them wrong and you'll spend months untangling cost reports and compliance audits.
Get them right and your finance team will actually understand your Azure bill.
Next time: I'll show you the KQL queries I use to audit tag compliance and generate clean cost reports. Because great tags are only useful if you can report on them effectively.
Have tag horror stories or questions? Hit me up at david@azure-noob.com - I've probably made the same mistake.
